The ability to use the product itself to get new visitors is one of the most exciting aspects of growth hacking. Pulling visitors into the top of your funnel is good, and so is pushing them in, but there is something magical about using the product itself to drive traffic. When done well, it can have a compounding effect which cannot be replicated with push and pull methods alone.
For instance, if you utilize the pull method of creating an infographic then you can expect to get traffic, but the inbound visitors to that infographic will decrease each day and eventually level out at a relatively low number. Compare that with some of the product tactics listed in this chapter. It’s possible, using the product itself, that each time someone comes to your site they bring their own network of relationships into your funnel as well. This is where the idea of viral loops come into play. If you are able to use a product tactic in such a way that for every visitor that enters your product, they bring along more than one other person into your product, then you’ve created a viral coefficient of over 1 (sometimes referred to as K). You’ve achieved exponential growth. You’ve gone viral.
However, I need to caution you at this point. Most products don’t go viral. If you are trying to growth hack a B2B enterprise product then I highly doubt that you will have a viral coefficient anywhere near 1. Not because you’re doing something wrong, but because it’s just hard to use these tactics in certain markets. Even if you have a consumer facing product virality is still extremely difficult.
So how should you view these tactics? If it really is that hard to get a K factor of 1+ then should you just scrap the product as a strategy for getting visitors? Absolutely not. Any K factor above 0 will positively impact all of your other marketing efforts, even if it never approaches the illustrious 1+. Let me explain.
If you have a K of .5, then this essentially means that for every one new visitor to your product they bring half a person into your funnel. 10 new visitors actually becomes 15. This isn’t virality because it doesn’t keep going up and to the right exponentially, but you’re still bringing new people in that wouldn’t have seen your product. Consider the pull method of creating an infographic in this light. If you bring 500 people into your product this month because of an infographic then this actually becomes 750 people with a K of .5. You’ve amplified a pull tactic by using a product tactic. That’s how to think about product tactics. They amplify anything that comes into your funnel.
A K factor of .5 also means that if you’re using the push tactic of purchasing ads then you can spend less to get a certain number of visitors because every 10 ad clicks becomes 15 visitors. Saving money is obviously a good thing, but this also allows you to pay more per click, and possibly outbid competitors. Remember what we said in the last chapter. Ads are just a business model competition and your product tactics, which amplify your product activity, strengthen the efficiency of your business model.
Network Invitations
We now live in a world where many people have already compiled their social networks in various places. We have a group of friends on Facebook. We follow people on Twitter. We are connected to business relationships on LinkedIn. We have a list of email addresses in Gmail. We have the phone numbers of friends and family in our mobile phones. The first product tactic that we’ll discuss for getting visitors hinges on our ability to use pre-existing, pre-defined, networks of relationships to our advantage.
Phone Contacts
If you are building a mobile app then you are basically a few clicks away from permission to message their entire phone book about your app. We don’t usually think of a phone book as a social network, but it might be our most intimate network of relationships. Umano, a new service that provides the ability to listen to popular online articles, utilizes this tactic. They prompt you to share with friends after using their service a couple of times, or you can do so from the settings menu (below). Notice how they preselect everyone for you, and you have to either manually deselect people or “unselect all.” This is a common practice for many of the network invitation tactics. It is also worth noting that you can call or text with access to a phone number, so this gives you a few options on how to message people once you’ve gained permission. There might also be email addresses associated with a phone number that you can also access.
Email Contacts
Another network which people have already developed, that we can use to our advantage, is their email contacts. This was much more popular a few years ago, but variations of it are still possible. LinkedIn allowed you to import your email addresses, which they would subsequently message, and this jump started their initial traffic.
Social Contracts
Besides phone books and email contacts, the third kind of network that we can leverage is social contacts. Twitter, Facebook, LinkedIn, Instagram, Pinterest, and more, are all networks where we’ve created a social graph. We have existing relationships which can be invited to a new product. It’s difficult to target every social network because people probably won’t give you access to all of them, but one can be enough. Focus also helps you make technical decisions about your own product. If you know that you are going to use Facebook as the primary social network for inviting new users into your product then this might cause you to use Facebook Connect as your product login. This means that it will be fewer clicks on the end user, and less friction, when you ask them to invite their Facebook friends later. Below is the example from the Facebook developer documentation of what a friend invitation screen looks like.
Social Sharing
Social sharing, as defined here, is not about explicitly inviting people into your product via their established connections or friends. This tactic is more about allowing anyone to talk about your product on their social network for whoever may be reading it. For instance, instead of asking someone to invite their Facebook friends to use your product, you instead allow them to easily post something to their Facebook feed about your product. If they have a public profile then this can be seen by anyone, not only their friends. The most prevalent example of this is seen in popular blogs. The Next Web prominently displays the ability to share each and every post with your social connections in various places.
Most social networks have code snippets that you can copy and paste into your product to make this kind of social sharing extremely easy. There are also solutions that combine all the popular social sharing options into a single interface.
Although it may not be obvious at first, another thing to keep in mind when implementing a social sharing strategy is to consider where your traffic naturally comes from. If you get most of your inbound traffic from Twitter, but you only allow people to share your product on Facebook then you are missing an easy opportunity. Make sure that people can share your product in the places that are most likely to bring you back more inbound visitors. This will have a compounding effect.
API Integrations
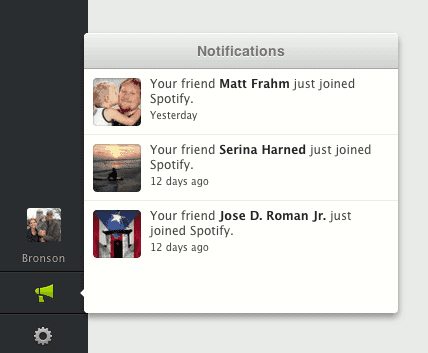
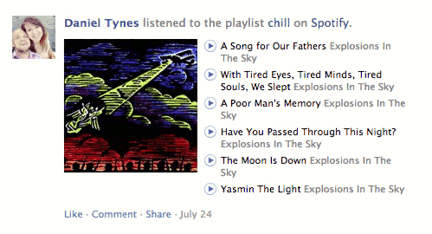
The next step, beyond social sharing, is to actually integrate your product with an existing social network at the API level. Instead of just asking them to share, you can actually bake sharing into the experience and make it happen in the background without forcing the user to give you permission each time. A great example of this is Spotify. It’s no secret that Spotify heavily used Facebook to grow their product, and they did so through an API integration. Once you login to Spotify using Facebook Connect and give Spotify the needed access, then your activity on their service is automatically published to your Facebook feed, and it’s also published inside of the Spotify app to anyone that you are connected with on Facebook. Below is a screenshot of the Spotify app, notifying me of new users who are also connected to me on Facebook, and another screenshot showing notifications within Facebook itself of my friend’s listening habits. These are done completely in the background, which creates frictionless sharing that can only really happen through an API integration.
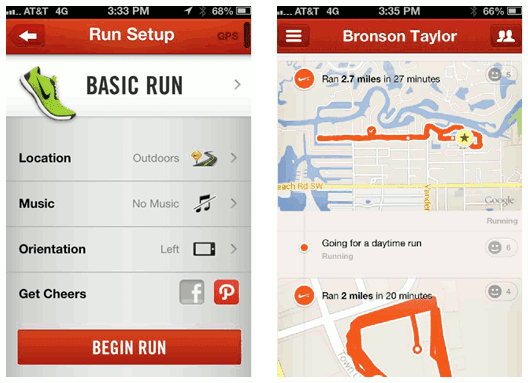
Another example of this tactic is the Nike+ API integration with Path and Facebook. Everytime I go for a run and track it using the Nike+ app on my phone, then the data about my run is pushed to Path and Facebook, so that my friends can see my activity. Friends can even cheer me on from within Path or Facebook which will trigger an applause sound as I run. This is borderline genius. Below you can see my Nike+ app asking me to share on Path, and on the right you can see the results being published to my Path friends. Again, this it totally seamless. Once I set it up initially it does this automatically.
API integrations, despite their incredible upside, are not 100% stable. As certain products become extremely popular, and gain momentum on existing social network, then it is not entirely uncommon for exposure to be throttled. Facebook, for instance, has the incentive to give you access to their platform. This keeps them in a dominant position if many developers use them. However, Facebook does not have incentive to give you the complete social graph of their billion users. If you start to have too much success with an API integration then you can’t count on the rules staying the same for you.
On a similar note, API integrations are great as a way to growth hack your product, but the more you intertwine your product with a 3rd party service, the more at risk you are. Twitter is a great example of this. Many companies were built on the Twitter API, but then Twitter changed the number of API calls allowed. This left many Twitter clients without a backup plan. Use APIs to grow your product, but be wary that the API doesn’t become your product.
Powered By Links
One of the first examples of product growth hacking actually used the powered by link tactic. When Hotmail first came out they did something that was simple, but which would drastically change their trajectory. They included a link at the bottom of emails that were sent using their service that said “Get your free email at Hotmail.” A viral loop was born.
This tactic is still being used to this day. A modern example is found in services that allow you to embed a popup on your website for various reasons. Widgets of any kind are good candidates for these powered by links.
Incentives
Certain products lend themselves easily to creating incentives for users to bring new people into the product. The classic example of this is Dropbox. They have a number of incentives that they offer users for various actions that they can take. This tactic works especially well if you have something which is of low cost to you, but of high value to users. In Dropbox’s case, they use storage space like a currency because the exchange rate is in their favor. Storage is not that expensive, but getting new users is very valuable to them. The user is in the opposite situation. Storage space is valuable to them, and their contacts don’t seem that valuable. This makes for a perfect storm.
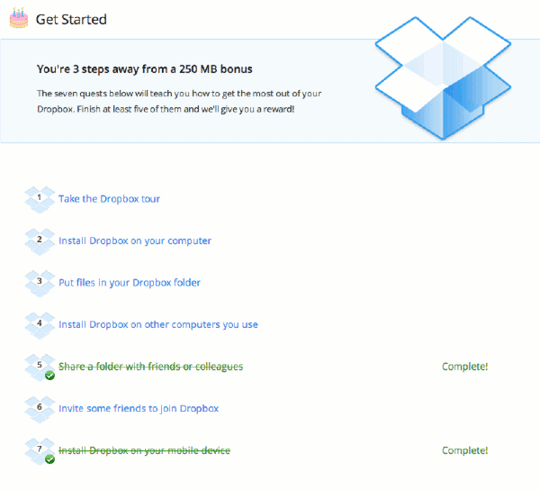
It’s worth cautioning that many startups, in an attempt to imitate Dropbox, have been frustrated with their inability to pull off the incentive tactic. Their product might not have much intrinsically to offer their users as incentives. Also, notice that Dropbox goes beyond just giving away storage for friend invitations, but they also give away storage for actions that will help you understand their product. Educated users churn less.
Organic Viral Growth
As much as technology within the product can spread the product, there is something that can be even more effective, organic word of mouth. Organic word of mouth is when someone shares your product, online or offline, in ways that you didn’t orchestrate. They are compelled to tell people whether you incentivized them or not. Organic communication can’t be measured, and it can’t be controlled, but it can be a force that propels your product forward. You can’t make someone share your product organically with their coworkers or friends and family, but you can do certain things to make it more probable. These types of products all tend to spread organically:
- Simple
- Beautiful
- Pain relieving
- Products that make people look cool
- Emotional
- Fun
- Unique
- Surprising
You can’t be all these things, but you must be one of these things, or you probably don’t have a chance of spreading organically.
Read more here - http://review-and-bonuss.blogspot.com/2019/04/viral-hacking-to-get-hypergrowth.html


No comments:
Post a Comment